Table of Contents
About the Author(s)
Aqsa Rehman is an International Relations scholar currently pursuing her Master’s degree at Kinnaird College for Women. She completed her Bachelor’s in International Relations from Lahore College for Women University (LCWU). Her research interests focus on analyzing the intersection of advanced technological tools with contemporary international and domestic political issues, bringing fresh perspectives to the evolving dynamics of global politics in the digital age.
Abstract:
In the past, the only security concern for Pakistan was its territorial security but in the past 20 years Pakistan has gone through so many issues that the securitization policy of Pakistan has changed over time and new dimensions of security are being added in the domain of securitization and the element of ‘Human Security’ was added in the National Security Strategy of Pakistan just a few years back. Out of the other many non-traditional security issues which Pakistan tends to face is the issue of Cyber Security. With the emergence of technology and increasing globalization of the world, Pakistan is also a victim of cyber warfare. The use of smartphones and internet applications has become very common and people have put so much of their personal information just ‘out there’ that it has become easy for hackers to get this information. This paper will analyze the use of cyberspace in Pakistan by its adversaries and what’s done and what needs to be done to secure it. It also analyses the consequences Pakistan could face if these issues are left unsolved. This is descriptive research and secondary resources are used to support it.
Keywords: Pakistan, Cyberspace, Human Security, Cyber Security, Securitization
Introduction:
Since its creation Pakistan has not been a stable country, a country which was envisioned to be a democratic state has not seen a single stable democratic regime. This affected both the internal and external policies of Pakistan thus affecting the security (both traditional and non-traditional). From border clashes with India and Afghanistan to the decline in economic conditions of the state. From terrorism to Climate change and now the threat of fifth-generation warfare Pakistan has seen both traditional and non-traditional security threats in the past 20 years. Every issue had an immense effect on Pakistan and its citizens and thus we cannot claim that any one particular issue has led to the conditions Pakistan face today.
A matter of security becomes important when it starts to threaten the sovereignty and the existence of the state. Since its creation Pakistan considered only one issue as a threat which was the security of borders thus its policies were designed to specifically address those issues but as soon as the 21st century started new security threats which were non-traditional started to emerge thus Pakistan’s foreign policy also changed. In Pakistan’s National Security Strategy of 2018, the aspect of ‘Human Security’ was also added.
Non-Traditional Security Issues in Pakistan:
In the past twenty years, Pakistan has faced various non-traditional security issues. Starting from terrorism to economic crises to poverty and now with the advancement in the field of science and technology, the abuse of cyberspace has also become an important security concern. One of the far most important security concerns for Pakistan at present is the issue of cyber security.
Cyber Security and Cyber Space:
Cyberspace is used as a tool to harass people, to threaten them, as a propaganda machinery by various non-state actors and political parties and so on. It is such a vast and complex term and it is yet not described completely what kinds of crime come under the domain of cyber-crime.
It is defined as:
“Offences that are committed against individuals or groups of individuals with a criminal motive to intentionally harm the reputation of the victim or cause physical or mental harm to the victim directly or indirectly, using modern telecommunication networks such as the Internet. (Chat rooms, emails, notice boards and groups) and mobile phones (SMS/MMS)”. (Usman, 2018)
However, it has become very vast in its operation and has included many other forms of crime as well.
Norbert Wiener used the term ‘cyber’ as a prefix in his book ‘cybernetics’ for the first time. Since then this term is used for anything related to information and technology.
Cyber security on the other hand means addressing these issues of cybercrime through some appropriate measures and strengthening the safety of cyberspace.
Emergence of Cyber Space:
The use of cyberspace emerged in Pakistan in the early 21st century and it increased vastly in the last decade. Advancements in technology have made cyberspace an integral part of our society. It has replaced various other mediums of information such as televisions and newspapers. Our day starts with checking Twitter for the latest news updates and ends up with watching some shows on YouTube for entertainment. With almost every kid having his own personal smartphone and having social media accounts it has become necessary to keep a check on cyberspace. As this medium gained importance its abuse cannot be neglected either. Cyberspace has been used and abused in the last decade in Pakistan. Pakistan ranked in 9th position in developing digital economies as per the UN Conference on Trade and Development‘s Information Economy Report. Pakistan telecommunication authority notes that around half of Pakistan’s population uses broadband internet services.
Cyber Space: A Tool for the Enemy:
The cyberspace is not secure internally as well as externally in Pakistan. Just like in other strategic theatres cyberspace is another strategic theatre for Pakistan and India to work against each other. Both states use cyberspace to hack each other’s systems with the most recent example being of 2023 when the Indian hackers hacked more than ten embassy websites of Pakistan as a response to Pakistan’s breach into Indian Cyberspace. False trends on twitter to create panic is another tool used by India against Pakistan. This cyber space rivalry is a relatively new domain for Pakistan and India but it can prove to be more deadly than the wars which are fought at the borders. (Shankar, 2023)
Figure 1.1
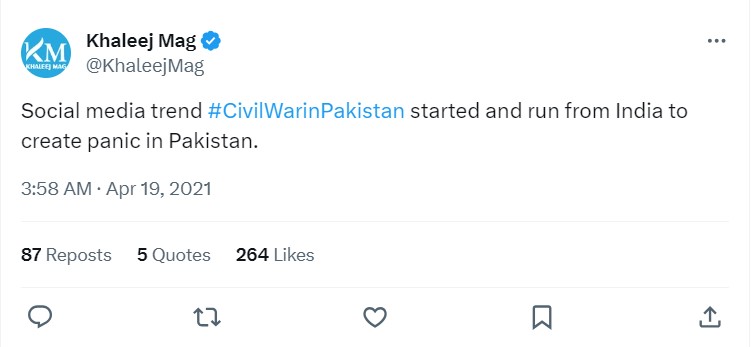
Source: Twitter/ X
Cyber Space is also being used in Pakistan to promote terrorism, fuel anti-Pakistan sentiments and inculcate extremism in the society. Organizations such as Tehreek-e-Taliban Pakistan (TTP) and Balochistan Liberation Army (BLA) use Twitter to promote their agendas. They promote violent activities, justify them and also gain support through their regular tweets. It is often seen that they try to frame themselves as heroes after a terrorist attack has happened. In 2015, the Pakistan Army detected a network of women who gathered their supporters through the use of cyberspace. This network was working for ISIS.
Furthermore, Tehreek-e-Labaik Pakistan has used Twitter to spread its message to society. It has encouraged people to protest in the past five years. Actually cyberspace is commonly used as a propaganda tool by political parties against other political parties.
Cyber espionage has become a very threatening concern for the security of Pakistan. Various malware are used by India as well as by the political elites of Pakistan to gain access to high-profile information. Imran Khan is said to be a victim of one such malware known as the
Pegasus. This can infiltrate a person’s mobile phone by a phone call or a mere message. Internationally, India deployed two malware to spy on Pakistan Army officials and also tried to attack the nuclear facilities. (Muhammad Nadeem Mirza, 2022)
Security Framework of Pakistan’s Cyber Space:
As the use of technology emerged in the early 2000s, Pakistan passed its first Electronic Transactions Ordinance in 2002. FIA established the National Response Centre for Crimes in 2007.
Later on, legislation was done to secure the cyber space. In 2016, the Prevention of Electronic Crimes Act was passed by lawmakers. At first, the issue of cyber security was included in the national action plan but in 2021, Pakistan took a step forward in securing cyberspace and a National Cyber Security Policy was formulated. The same year Personal Data Protection Bill was also passed. In this bill, it was accepted that privacy and free communication is the right of every individual. Thus their personal data would not be breached. (Iqbal, 2023)
Inter-relation of Cyber Security with other Forms of Security:
Cyber warfare is not fought on land but it can lead to more deadly consequences. A hacker can hack the personal information of military or other high-profile personnel. They can have access to highly secretive data yet their identity would be unknown. The one being attacked won’t even know until the job is done. Hackers can have access to military information, they can breach the system of any army unit, can cut off power from an electric grid as well as attack a nuclear facility. If all these factors are combined together in the case of Pakistan and India it can lead to a full-fledged war. This is a very serious concern for global security as well as the security of Pakistan. India can plan and launch an offensive against Pakistan by controlling and destroying its system first and then attacking on borders. In this way a non-traditional security issue could lead towards a conventional war. Although it is not possible because the military information is kept very secure although hacking and data breaches were seen at higher levels but it never reached to something this serious and was always controlled. But still this aspect of cyber security can’t be denied.
On the other hand, it also culminates the threat of another non-traditional security issue which is terrorism. As already discussed cyber-space is used as a propaganda machinery to manipulate the minds of young people and to justify their own actions.
A Tool for 5th Generation-warfare:
Cyber Space is being used as a tool for 5th generation warfare by non-state actors. Inflicting hate against their own states, glorifying the acts of violence and self-harm. Facebook and Twitter are mainly used by these organizations. Fake and paid Twitter trends promote an image that these steps are supported by the vast majority. It was also noted that most of these accounts are run by European states. With the advancement in technology, these terrorist regimes have hired well trained and well-educated people to promote their propaganda. The youth is being brainwashed without even knowing. (Rakhshani)
Figure 1.2

Source: Hussain Haqqani on Twitter/X
India also promotes and supports these terrorist regimes against Pakistan. Their news channels on electronic media write pro-terrorist regime articles and try to manipulate the minds of the general public. Such an example is the following headline of an article published by India Narrative.
This headline is trying to portray a Baloch Liberation Army terrorist who attacked three university teachers in Karachi, as fearless freedom fighters.
Figure 1.3

Challenges:
People are not aware of the issue of cyber-security. Many of the internet users are less educated and most of them are even under age. While using social media they are not aware of the probabilities of their data getting breached. Most of them often over-share which can eventually lead to the breach of their data.
People are not aware of the propaganda techniques to understand that their minds are being manipulated. The young population easily gets attracted and impressed by these techniques used by terrorist regimes as well as political parties and thus they easily become a tool for these organizations to achieve their motives.
Despite the legislation and various ordinances, not much has been achieved till now in the realm of cyber security. A better implementation framework is required for this purpose. Most of the time, the protectors are actually the breachers of data. In Pakistan, we have seen in various instances that personal data of citizens was breached due to some reason. So it is important to ensure that the data of citizens and their personal information is not accessed by anyone.
Analyzing the Threats to Pakistan’s Cyber Space:
At present, cyber warfare is a greater threat than the conventional warfare. This is because, in conventional warfare, the enemy is known. If Pakistan and India are at a conflict they would know that their enemy is equipped with what kind of weapons and so they will prepare themselves well. But in cyberspace neither the enemy is known nor his ability. A state wouldn’t even know until the job is done. Also Pakistan and India are less likely to go on a land offensive because of various reasons including the nuclear capabilities of both but they can inflict losses on each other with the use of cyberspace.
Making laws is not enough until they are implemented. Pakistan lacks the machinery to implement these laws. Also, Pakistan’s political elite is itself found guilty of the breach of the personal data of the citizens as well as their political rivals. This gives an insight into how the security framework for Cyberspace works in Pakistan.
Cyberspace is also being used as a piece of propaganda machinery to inflict fear and hatred for Pakistan. This is done by both state and non-state actors as well as the political parties at times. Steps needs to be taken in this regards as well. The people behind these profiles should be taken into account. Serious actions should be taken and their accounts should be restricted from these social media platforms. But we need to look at this issue from other aspects as well. Why people are easily brainwashed? This is because there are certain groups in our country which are not getting their due share of rights. Thus, they easily get influenced by such propaganda machinery of non-state actors. If we want our people to stop getting influenced by these extremist regimes we need to address their grievances which leads them to follow these regimes first.
At last, as security is not a segregated issue but is strongly interlinked in a complex web, if security in any one field is compromised it can have an adverse effect on the other forms of security as well. Thus if we want to ensure our territorial as well as internal security it is very important to ensure cyber security because compromise on cyber security can lead to compromise on other forms of security as well which would eventually affect Pakistan.
Conclusion:
Cyber warfare is not fought in a strategic theatre thus it is not an easy task to limit the enemy to a certain boundary. A state can have the safest technological system yet can be attacked by hackers. As Pakistan is prone to such threats because both India, its arch rival, and its comparatively new enemy which is the Balochistan Liberation Army are using this mode to inflict damage to Pakistan. Both through malwares and through the use of Propaganda. Thus the cyber space can be violated in two ways either through the breach of data and getting personal and high profile information or using propaganda to manipulate the minds of the people and the spread of false information to inflict fear among the locals. Stricter measures are needed to be taken in this respect and the access of these non-state actors should be limited. If not done at the right time, this can lead to grave consequences leading to other traditional and non-traditional security concerns as well.
References
Iqbal, G. (2023, June 21). Assessing Pakistan’s Cyber Security Landscape. Retrieved October 1, 2023, from Modern Diplomacy: https://moderndiplomacy.eu/2023/06/21/assessing-pakistans-cybersecurity-landscape/
Mir, A. (2022, January 12). Afghanistan-Pakistan Border Dispute Heats Up. Retrieved October 1, 2023, from United States Institute of Peace: https://www.usip.org/publications/2022/01/afghanistanpakistan-border-dispute-heats
Muhammad Nadeem Mirza, M. S. (2022, 9 20). 3-Cs of Cyberspace and Pakistan: Cyber Crime, Cyber Terrorism and Cyber Warfare. Retrieved October 1, 2023, from issi.org: https://issi.org.pk/wpcontent/uploads/2022/09/4_SS_Muhammad_Nadeem_Mirza_and_Muhammad_Shehzad_Akra m_No-1_2022.pdf
Pakistan lodges strong protest with India over airspace violation. (2022, March 11). Retrieved October 1, 2023, from Radio Pakistan: https://www.radio.gov.pk/11-03-2022/pakistan-lodges-strongprotest-with-india-over-airspace-violation
Rakhshani, M. A. (n.d.). Fifth-generation Warfare and its Challenges to Pakistan Mehmood Ali Rakhshani. Retrieved October 1, 2023, from Hilal English: https://hilal.gov.pk/engarticle/detail/NjI1Mg==.html
Shankar, S. (2023, May 18). Counter Cyber Attack: Indian Hackers Retaliate, Paralyze 10 Pakistani Embassy Sites in the world DDOS drama. Retrieved October 1, 2023, from Times Now News: https://www.timesnownews.com/technology-science/counter-cyberattack-indian-hackersretaliate-paralyze-10-pakistani-embassy-sites-in-worldwide-ddos-drama-article-100322688
Timeline: Events of the Feb 2019 Pak-India aerial combat. (2020, February 26). Retrieved October 1, 2023, from https://www.dawn.com/news/1536224
Usman, M. (2018). CYBER CRIME: PAKISTANI PERSPECTIVE. Retrieved October 1, 2023, from iri.aiou.edu: https://iri.aiou.edu.pk/wp-content/uploads/2021/12/Cyber-Crime.pdf

